Kubernetes is ever growing and certainly a standard for container orchestration, however with it being picked up more and more by development teams, we want to ensure best practices and correctness of Kubernetes configuration files are valid. This can be tough and challenging to manage, let’s look at a tool that can assist you in this journey. Let’s look at Kubelinter, that will help you to validate Kubernetes YAML files, ensuring best practices are being adhered to and avoid those common pitfalls!
In this blog post, we will explore Kubelinter and how to integrate it into your CI/CD pipeline using GitHub Actions.
So, what is this Kubelinter tool?
Kube-Linter is an open-source project that is developed by StackRox. The tool analyses YAML files and provides feedback on potential issues, security vulnerabilities, and best practices. With its primary goal to help developers catch errors early in the development process, reducing the risk of misconfigurations and security vulnerabilities in production.
You are probably wondering, why should I use KubeLinter?
Well, using this as part of your development CI/CD workflow brings numerous benefits including:
- Enhancing Security: It will help to identify any potential security vulnerabilities and misconfigurations in your Kubernetes YAML files. It will check for common security issues, even for excessive permissions.
- Early Issue Detection: Including it as part of your CI/CD GitHub Action workflow, allows for early issue detections – which you can identify and rectify early in the CI/CD process, saving you time and potentially further problems down the development line
- Consistency across teams: Helping you to adhere to best practices, which will begin to foster consistency across development teams. Ensuring everyone follows the same Kubernetes configuration standards
- Best Practices: Enforces best practices for Kubernetes configuration files, checking for common mistakes, deprecated APIs and even missing or misconfigured probes
- Enhancing the code review process: All the above will lead to more effective reviews and improved collaboration
Key features of KubeLinter
- Linting for best practices
KubeLinter comes equipped with a set of predefined rules based on best practices recommended by the Kubernetes community. It ensures that your manifests align with established guidelines, promoting consistency and reliability.
- Customisable rules
While it comes with a set of predefined rules, it also provides the flexibility for users to define and enforce custom rules that align with the specific needs of their Kubernetes environment.
- Can integrate with your current CI/CD GitHub Actions workflow
Configuring KubeLinter with GitHub Actions
Let me show you how to now configure this, thanks to stackrox for providing this awesome example
Prior, ensure you have enabled this workflow permission as mentioned in this blog post
# Based of https://github.com/stackrox/kube-linter-action/blob/main/.github/workflows/kube-linter-sample.yml
name: Check Kubernetes YAMLs with kube-linter
on:
push:
branches: [ main, master ]
pull_request:
jobs:
scan:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Create ../results directory for SARIF report files
shell: bash
run: mkdir -p ../results
- name: Scan yaml files with kube-linter
uses: stackrox/kube-linter-action@v1.0.4
id: kube-linter-action-scan
with:
# Adjust this directory to the location where your kubernetes resources and helm charts are located.
directory: invalid
format: sarif
output-file: ../results/kube-linter.sarif
continue-on-error: true
- name: Upload SARIF report files to GitHub
uses: github/codeql-action/upload-sarif@v3
- name: Verify kube-linter-action succeeded
shell: bash
run: |
echo "If this step fails, kube-linter found issues. Check the output of the scan step above."
[[ "${{ steps.kube-linter-action-scan.outcome }}" == "success" ]]
Lets breakdown the 5 steps:
- uses: actions/checkout@v4
Fetches the repositories code into the workflow’s runner environment
- name: Create ../results directory for SARIF report files
shell: bash
run: mkdir -p ../results
This prepares directory where github/codeql-action/upload-sarif@v3 looks up report files by default.
- name: Scan yaml files with kube-linter
uses: stackrox/kube-linter-action@v1.0.4
id: kube-linter-action-scan
with:
# Adjust this directory to the location where your kubernetes resources and helm charts are located.
directory: invalid
format: sarif
output-file: ../results/kube-linter.sarif
continue-on-error: true
This utilises the “stackrox/kube-linter-action@v1.0.4” GitHub Action to scan YAML files using the kube-linter tool. It specifies the directory where the Kubernetes resources and Helm charts are located (currently set to “invalid”), sets the output format as SARIF, defines the output file path as “../results/kube-linter.sarif“, and continues the workflow even if errors occur. (In this example, is using incorrectly formatted content)
- name: Upload SARIF report files to GitHub
uses: github/codeql-action/upload-sarif@v3
Uploads SARIF report files to GitHub using the “github/codeql-action/upload-sarif@v3” GitHub Action.
- name: Verify kube-linter-action succeeded
shell: bash
run: |
echo "If this step fails, kube-linter found issues. Check the output of the scan step above."
[[ "${{ steps.kube-linter-action-scan.outcome }}" == "success" ]]
Verifies the success of the kube-linter-action by checking the outcome of the scan step and displaying a message if any issues were found.
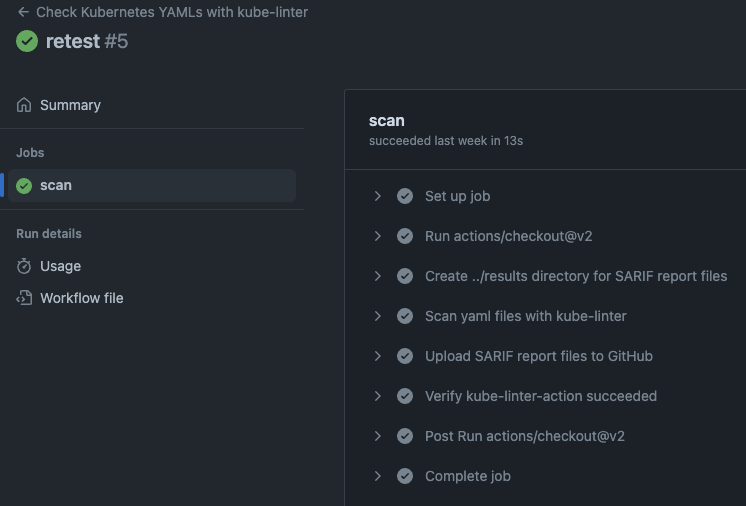
The below shows a successful run!
What happens when Kube-Linter validation is not correct?
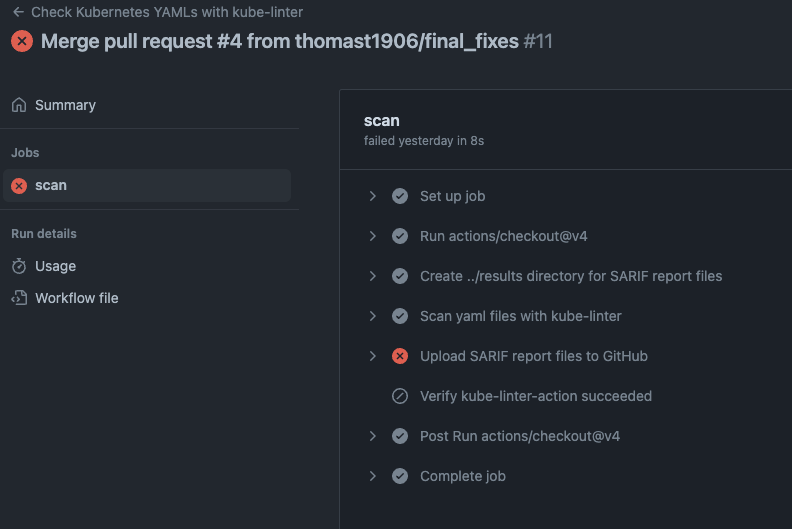
The GitHub action shows as a failed run, lets look further into this step: Upload SARIF report files to GitHub
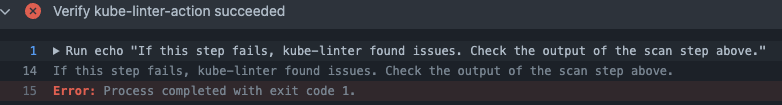
Looking below will show you what happens when you see this, its great!
GitHub Security Code Scanning Vulnerability Alerts
As part of the workflow, we have uploaded a SARIF report to the GitHub repository. This report contains the results of the kube-linter scan, including any validation issues that were detected – now once you have a validation issue with kube-linter, it will appear in GitHub as below.

This is awesome, selecting any and going into the vulnerability gives you even more detail and allows you to create an issue – a feature I do find great!

Certainly let Kubelinter streamline your Kubernetes development journey – paving the way for more secure, efficient, and best-practice-compliant deployments to your Kubernetes clusters!
GitHub repository with all example content
