The story
I have created this blog to detail and describe how a Network Policy Server (NPS) is used to integrate with an Azure VPN gateway using RADIUS to provide Multi-Factor Authentication (Azure MFA) for point-to-site connections to your Azure environment.
The process that will be documented in this blog:-
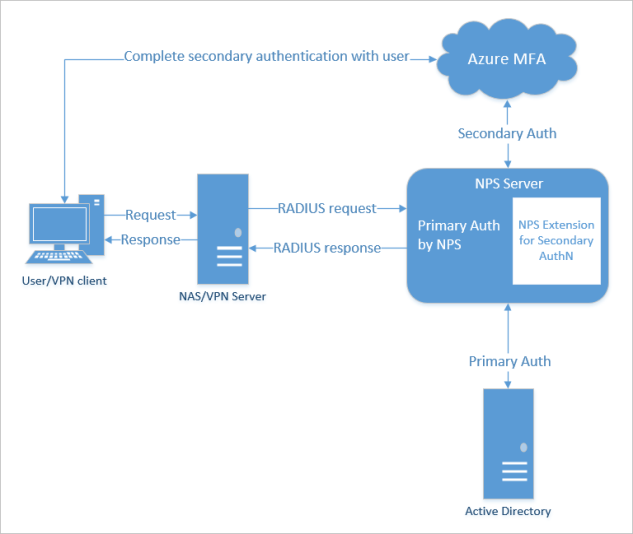
- Image Reference: docs.microsoft.com
Prerequisites
- Azure AD Connect Installation File
- Azure NPS MFA Extension File
- Active Directory Group Created that contains Active Directory Users who will be using the NPS/VPN connection
- Gateway deployed on Azure environment
Installation
The installation steps have been split into areas:-
- Azure AD Connect Installation
- Setup an Azure AD user with MFA
- NPS Extension Installation
- NPS Configuration
- Gateway Configuration
Note:- The Azure AD Connect installation & NPS extension installation will happen on your NPS server. I will include a troubleshooting section which may become useful during this.
Azure AD Connect Installation
Launch the installer downloaded above, for this blog I will be installing use the Express Settings:-
- Click “Use Express Settings” & select next
- Enter the Azure AD Username & Password:- this Azure AD user will be part of the Azure AD that you will be using to be sync the local AD users to
- Local AD DS Username and Password will be prompted (Admin Account)
Once installation has been completed successfully, a full synchronisation will be started of your local AD into the Azure AD. This most likely will not be a requirement for you, it can be changed as part of the setup process but I have added this below on how to only synchronise the AD users that you want to have Azure AD MFA configured.
- Open “Azure AD Connect” icon on your desktop
- Click “Customize synchronization options”
- Enter Azure AD Username & Password
- Ensure correct Forest is selected
- Select the OU which has the users that will be synchronised to Azure AD
- Select next:- ensuring Password hash synchrization has been ticked
- Click Configure
Synchronisation will take place to Azure AD, 30 minute interval:- this can also be forced, I will discuss this in potentially a later blog.
Setup an Azure AD user with MFA
Follow this url to setup AD user with Authenticator app
Further instructions on how to setup
Ensure verification option by default is: Notify within application

NPS Extension Installation
- Click on Azure NPS extension .msi and agree to Terms & Conditions
- Once .msi has been installed, PowerShell commands are required to be ran:
-
cd "C:\Program Files\Microsoft\AzureMfa\Config"
-
.\AzureMfaNpsExtnConfigSetup.ps1
- When prompt, select yes to all modules, these are the additionally required PowerShell modules part of the Azure MFA implementation process
- Enter Azure AD Username & Password – previously used during Azure AD Connect Installation
- Enter Azure AD Directory ID, this is the Azure AD that will be syncing the local AD users
NPS Configuration
- Open Network Policy Server, it should look similar to this:

2. Register NPS Server with Active Directory
- Right click NPS (Local) & select Register server with Active Directory

Radius clients will now be added, these clients will be the IPs of the Gateway within your vNET that you will be using for MFA Authentication via Radius. within a /24 Subnet and using a Gateway – these IPs will be 0.0.0.4 & 0.0.0.5.
3. To add Radius Clients, select Radius Clients and Servers -> Radius Clients
Right click on Radius Clients and select New – Settings should be similar to below, with an adequate Friendly Name – also ensure to note down Shared Secret as this will be used for both your secondary Radius Client along with Gateway setup.

Now follow the same setup as above and create secondary Radius Client
A policy for your Azure-MFA VPN will now be created
4. Select NPS (Local) -> Under Standard Configuration – change drop-down to RADIUS server for Dial-Up or VPN Connections -> Select Configure VPN or Dial-Up

Below is a standard Policy – this can include additional configuration depending on the requirements you are working towards
Type of Connections

Radius Clients (Ensure both clients are added)

Configure Authentication Methods

Specify Users Groups
As mentioned as part of the prerequisites, add the user group that was created – this user group will be the users that will have authorisation to authenticate successfully.

Specify IP Filters
Defaults are used
Specify Encryption Settings
Ensure only Strongest encryption (MPPE 128-bit) has been selected

Specify a realm name
Defaults are used
Finish Setup
The NPS server has now been configured, next will be configuring the Virtual Network Gateway settings within the Azure vNET.
Gateway Configuration
- Open Azure Portal and select Virtual Network Gateway that will be used as part of the configuration
2. Select Point-to-site Configuration -> Configure Now
Point-to-site Configuration:-
Address Pool: VPN clients that connect to the VNet using this Point-to-Site connection receive an IP address from the specified pool.
Authentication Type: Radius Authentication
- Server IP Address: NPS Server IP
- Server Secret: Password used for Radius Clients within NPS configuration

3. Select Save -> Once setup has been completed, a VPN Client can be downloaded.
Additional information on how to install the client
Username: username@domain (testuser@tamops.test)
Password: Domain user password
The setup is now complete, I hope my blog has assisted in configuring Azure MFA with NPS – please contact me if you have any queries.
In my next blog, I will document some additional troubleshooting steps along with some automation for NPS
A connection to the remote computer could not be established, so the port used for this connection was closed. (Error 619) I keep getting this error. I didn’t use Active Directory.
I have disable all windows firewall both on my laptop and azure.
Probably failing trying to authenticate. Recommended to use with active directory
Great post. Thanks, Are you aware of any way to use this integration while allowing user to use hardware oath tokens. We have some users offer resistance to using the authenticator app
Hi Dan, thanks for commenting
See here in relation to your query :-
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/hardware-oath-tokens-in-azure-mfa-in-the-cloud-are-now-available/ba-p/276466