After a very exciting first day, back for another fast paced day in the world of Microsoft Ignite with again, quite a number of new additions/announcements to Azure.
Session: Architecting and implementing Governance across your subscriptions
Speakers: Joseph Chan
Governance is a requirement in any project, especially more and more sought after in today’s cloud world.
“Azure enables your organisation’s development and IT departments to be agile by making it easy to create, read, update, and delete resources as needed. However, while giving unrestricted resource access to developers can make them very agile, it can also lead to unintended cost consequences. The solution to this problem is resource access governance—the ongoing process of managing, monitoring, and auditing the use of Azure resources to meet the goals and requirements of your organization.”

Azure Governance can be broken into three main areas:
- Resource Organisation
- Control & Compliance
- Environment Deployment
100% of the top 300 Azure customers use policy. Azure Case study with BP to show how governance has assisted them.
Common guardrails – Leverage built-in initiatives and policies, examples of Azure Policies from GitHub

Session: Protect your cloud workload from threats using Azure Security Center
Speakers: Yinon Costica
Intelligent Security
- Identity and access management: Your universal platform to manage and secure identities
- Threat protection: Stop attacks with integrated and automated security
- Information Protection: Protect your sensitive data – wherever it lives or travels
- Cloud Security: Safeguard your cross-cloud resources

Common threats seen in the wild
VMs
- Brute force of open management ports
- Exploit through an unpatched vulnerability
Containers
- Exposed Kubernetes Dashboards
- RBAC not configured in the cluster
- Insecure container/host configuration
App Services
- Web shell deployment
- Reconnaissance attempts
SQL Database
- SQL injection vulnerabilities and attacks
- Access by a remote threat actor
Storage account
- Access by a remote threat actor
- Public access to storage accounts
Key Vault
- Harvest for secrets
- Permissive policies grant access to unneeded resources
Azure can assist with all these threats to minimise the potential attack vector including the following to help:-
- $1B annual investment in cybersecurity
- 3500+ global security experts
- Trillions of diverse signals for unique intelligence
Azure Security Centre can protect your workloads from threats, it uses industry’s most extensive threat intelligence to gain deep insights including:-
- Detect & block advanced malware and threats for Linux and Windows Servers on any cloud
- Protect cloud-native services from threats
- Protect data services against malicious attacks
- Protect your Azure IoT solutions with near real time monitoring
- Service layer detections: Azure network layer and Azure management layer (ARM)
Protecting Linux and Windows VMs from threats
Reduce open network ports
- Use Just-in-Time to avoid exposure of management ports
- Limit open ports with adaptive network hardening
Protect against malware
- Block malware with adaptive application controls
- Built-in Microsoft Defender ATP EDR
- Crash dump analysis and fileless attack detections
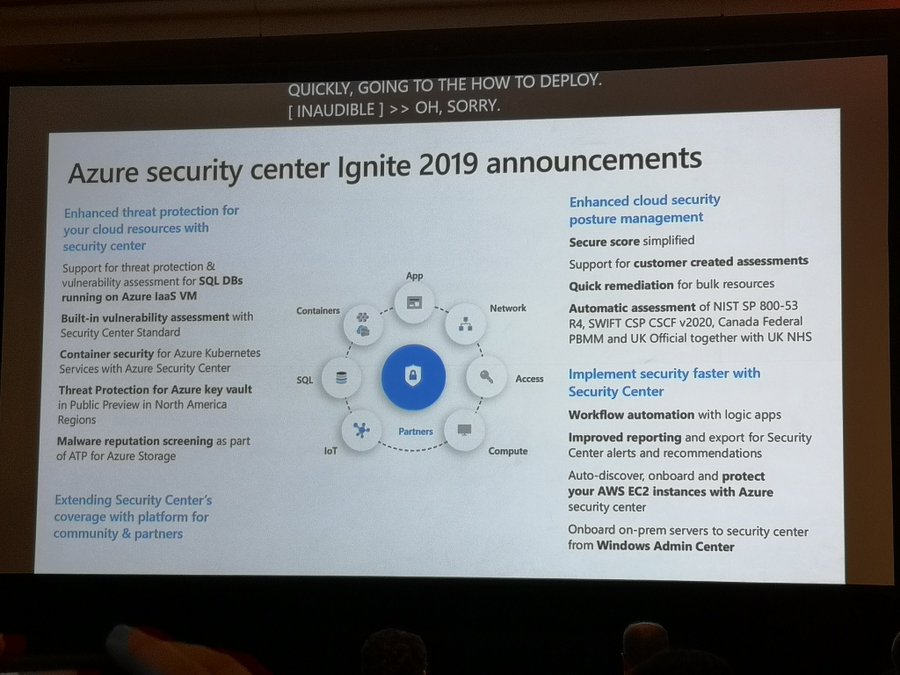
Announcement: Protect hybrid data centres and multi-cloud with Azure security centre
- Hybrid Service protection for Datacenters and other clouds
- Onboard on-prem servers to Security Center from Windows Admin Center
- Auto onboard AWS EC2 instances using new API connector (Preview)
Announcement: built-in vulnerability assessment for VMs
- Automated deployment of the vulnerability scanner
- Continuously scans installed applications to find vulnerabilities
- Visibility to the vulnerability finds in Security Center for portal and APIs
Announcement: Built-in vulnerability assessment for container images
- Seamless deployment and configuration of the vulnerability scanner
- Scan container images for vulnerabilities upon push to an ACR
- Visibility to vulnerable ACR container images including vulnerabilities details, severity, classification and guidance to remediation
Protecting AKS
- Actionable recommendations based on AKS best practices
- Cluster and Node Threat detection based on AKS audit log and Node Autid

New advanced protection capabilities for data services
- Protect SQL servers on Azure VMs: Vulnerability assessment and Advanced Threat protection to prevent and detect threats across SQL estate in Azure
- Malware reputation screening for Azure Storage: Detect advanced threats in Azure Storage with hash reputation analysis upon upload
- Advanced Threat Protection for Azure Key Vault: Detect unusual and potentially harmful attempts to exploit Key Vault
Session: PowerShell unplugged with Jeffrey Snover and Jason Helmick
What a session, from start to finish – it was highly entertaining!
Demoing throughout new features coming from PowerShell 7..
- PowerShell non .exe install without admin user credentials
- GP out-gridview
- PowerShell Vault / Secrets Management
The rest of my day today spent time going through the Vendor hall – it is massive! Seeing what products that we may need to use.
